The idea of MEV (Miner / Maximum Extractable Value) is not new to the crypto community. It was first formalized in the paper Flashboys 2.0 in 2019 and has since sparked many discussions around MEV’s effects and solutions. Nonetheless, for the majority of DeFi users or even natives, the concept of MEV can be convoluted and far-fetched.
MEV is typically defined as the total amount of pure profit a miner can extract by manipulating the order sequence within a block space or via block re-organizations. However, just by this definition, we still cannot be certain what exactly MEV is.
Is it a fixed amount of money or is it a phenomenon (as we can often see phrases like preventing MEV)? How does MEV have to do with front-running, back-running, and other types of predatory arbitrage techniques as they are always associated with each other? Finally, and perhaps more importantly, how does MEV have to do with the users, how will the MEV potentially change the crypto ecosystem (or will it), and what are the solutions?
Let’s first start with a better definition.
What exactly is MEV?
The core of MEV has very little to do with the miners but has everything to do with order sequence manipulation or order optimization techniques. To understand this concept, let’s first take a look at the traditional CeFi market.
In the traditional market where a continuous order flow processing mechanism is being used, from a high-level perspective, orders are processed on a first-come-first-serve basis. Once the order matching server receives the trader’s order, it gets pushed into the matching engine immediately. In this system, after the orders are being received, the order sequence is set and deterministic, and therefore, the full economic value of order sequencing is preserved.
Nonetheless, readers can probably see that before the order reaches the exchange server, it is just another dark forest where the order sequence can be theatrically manipulated (in the US, it is banned by the SEC). Predatory traders can use various methods to decrease the latency between their server and the exchange server, gaining the unfair market information ahead of the other trades and thereby making their own predatory transactions to be executed at the right time for maximized economic rewards. This, in a sense, can be viewed as order manipulation via speed, where you simply get to the “checkpoint” faster, and it has been implemented for years in the traditional markets.
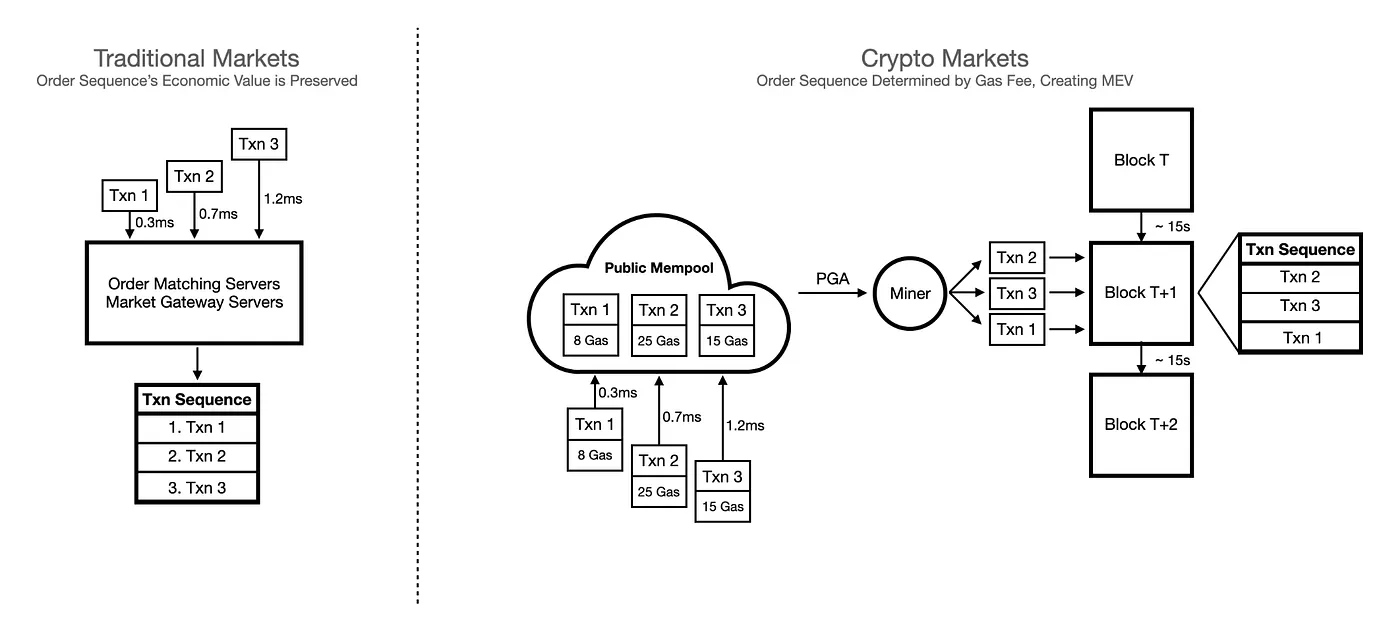
Crypto markets open up an entirely new paradigm for order sequence manipulation as the centralized checkpoint — the exchange servers (or the SEC) — are non-existent. Instead, for L1 blockchains (predominantly PoW and PoS blockchains), all transactions are sent into a public mempool where transactions are visible to everyone, and the transactions are ordered and packaged by miners through priority gas auction, or PGA, which simply means that the highest gas-paying transaction gets batched and executed first (and you can bid up the gas fee while the transaction is still in the mempool).
Essentially, this means that instead of trying to be fast, in the crypto world, predatory bots pay for the position on the ledger within a block space (which can seem like a more brute-force way of manipulating the order sequence. In practice, it is a bit more difficult than just to pay for the advantageous order position). By utilizing different bidding strategies, predatory bots bid up the gas fee so that their orders can be placed at the desired place as instructed by the predatory algorithms (front-running, back-running, sandwich attacks, etc.). This, in fact, is the most common flavor of the MEV, where the order sequence is being manipulated by the predatory bots and the economic value of the transaction sequence is transferred from the user to the predators. However, where do miners come into the play?
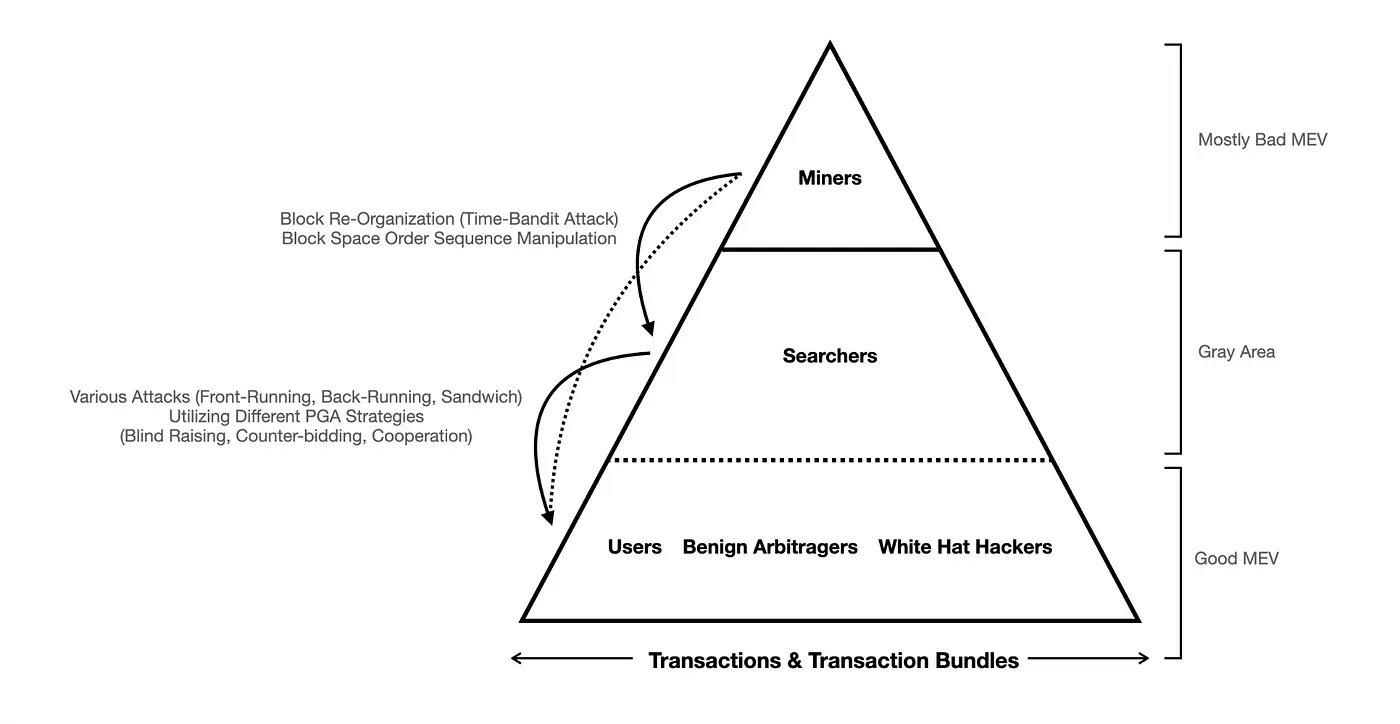
There’s a catch to the system, of course. We said previously that a centralized checkpoint is not present in the decentralized blockchain ecosystem. Well, it shouldn’t. However, if you inspect the plot above closely, you would notice that the group of miners is the only entity that has the power to determine whose and which order should be executed first within a block space. In this original design, PGA is simply one mechanism to help the miner to sort through a sea of transactions in the mempool. In other words, what predatory bots can do, miners can do with a lesser hassle.
Further, if there is residual MEV value in the past blocks, miners are incentivized to rebuild the entire block sequence and the transaction order so that they can reap the MEV profit. In order to pull off this strategy — also known as the “time-bandit attack”, 51% of the entire network’s hashing power is required, thereby endangering the consensus layer’s stability and decentralization level (notice here that this problem is universal in almost all consensus mechanisms, including PoW and PoS).
Lastly, as for the debate regarding what the M in MEV stands for, whether it should mean miner or maximum, both would make sense. They all mean that MEV represents the upper bound, or the total aggregate, pure revenue that can be generated from order sequence manipulation. Since the miners have the final say in this matter, we shall give them some credits.
Hence the MEV — Miner (Maximum) Extractable Value — the maximum value generated by manipulating the order sequence within a block space, exploitable by the predatory bots, but ultimately can be all reaped by the miners if they wish to do so.
How Bad is MEV Currently?
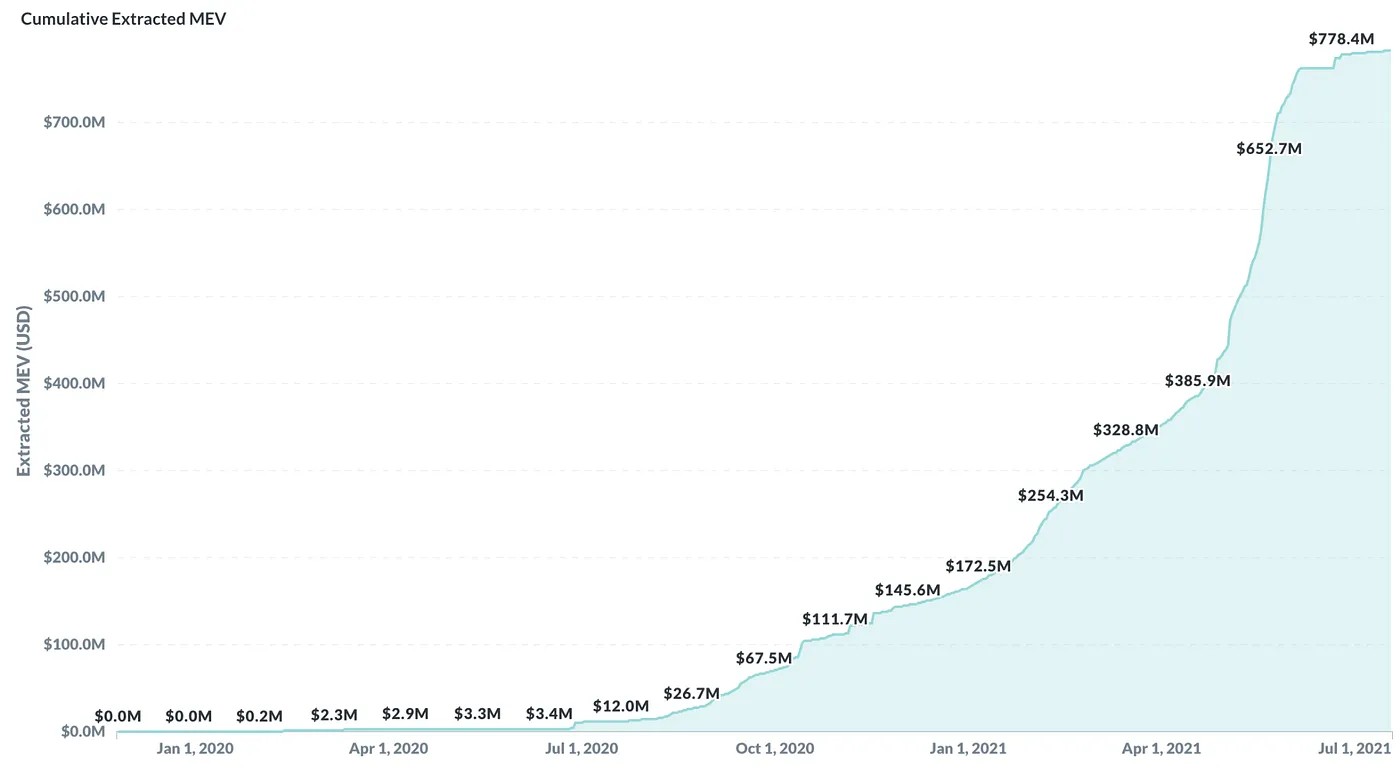
Thanks to the Flashbots team, we can have a sneak peek into the current state of the MEV / block space market. One thing to get out of the way first is that MEV is clearly real and growing.
The total tracked MEV value topped 778.4 million dollars, a shocking amount compared with just 1 year ago, a mere 12 million dollars (Figure 3). The aggregated MEV activities have also been wasting roughly on average 4% of the total gas usage of the Ethereum network, an increase from below 0.5% since last year this time.
On the daily level, regardless of the drawbacks that can be observed periodically, the MEV has also seen tremendous increase. The maximum amount of daily extracted MEV hit 6.1 million dollars on May 7, 2021, with the majority of the days in 2021 experiencing over 1 million dollars in the daily extracted MEV value.
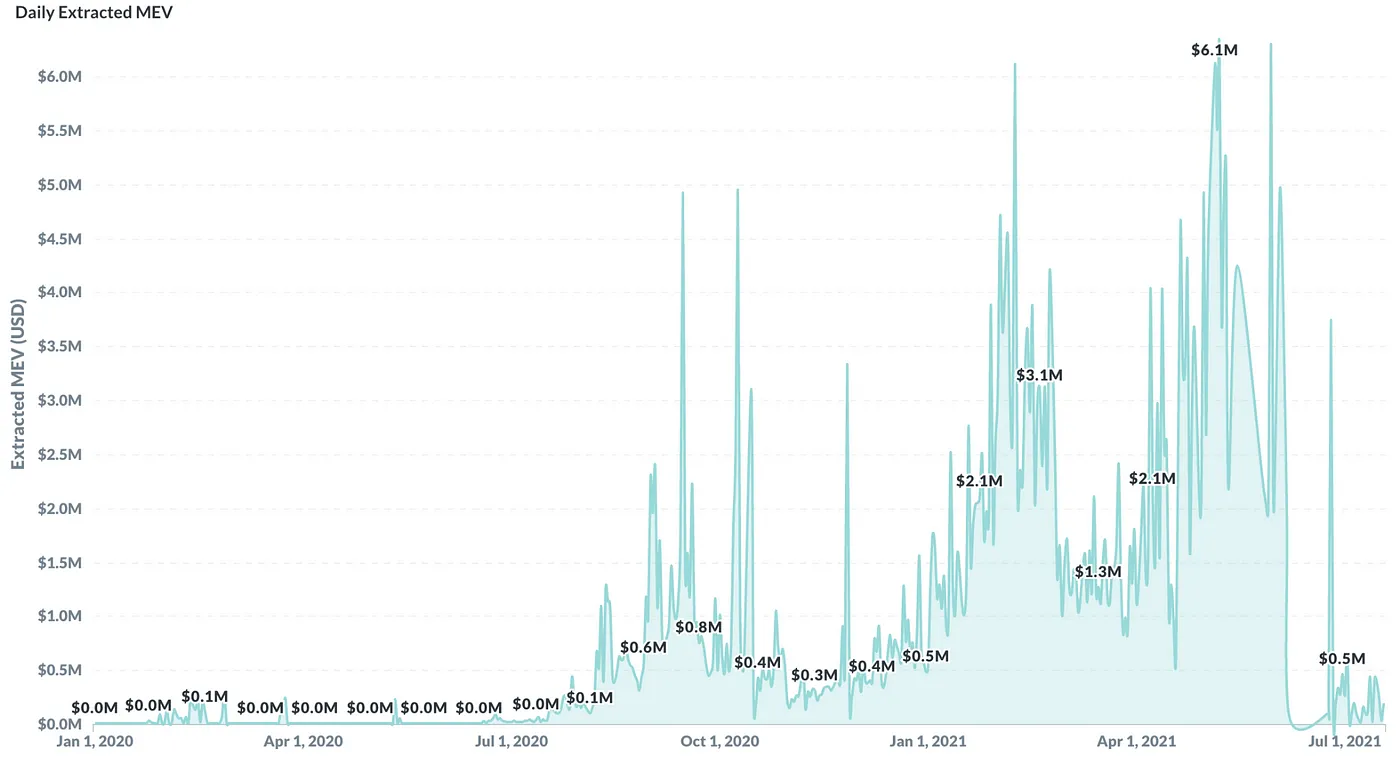
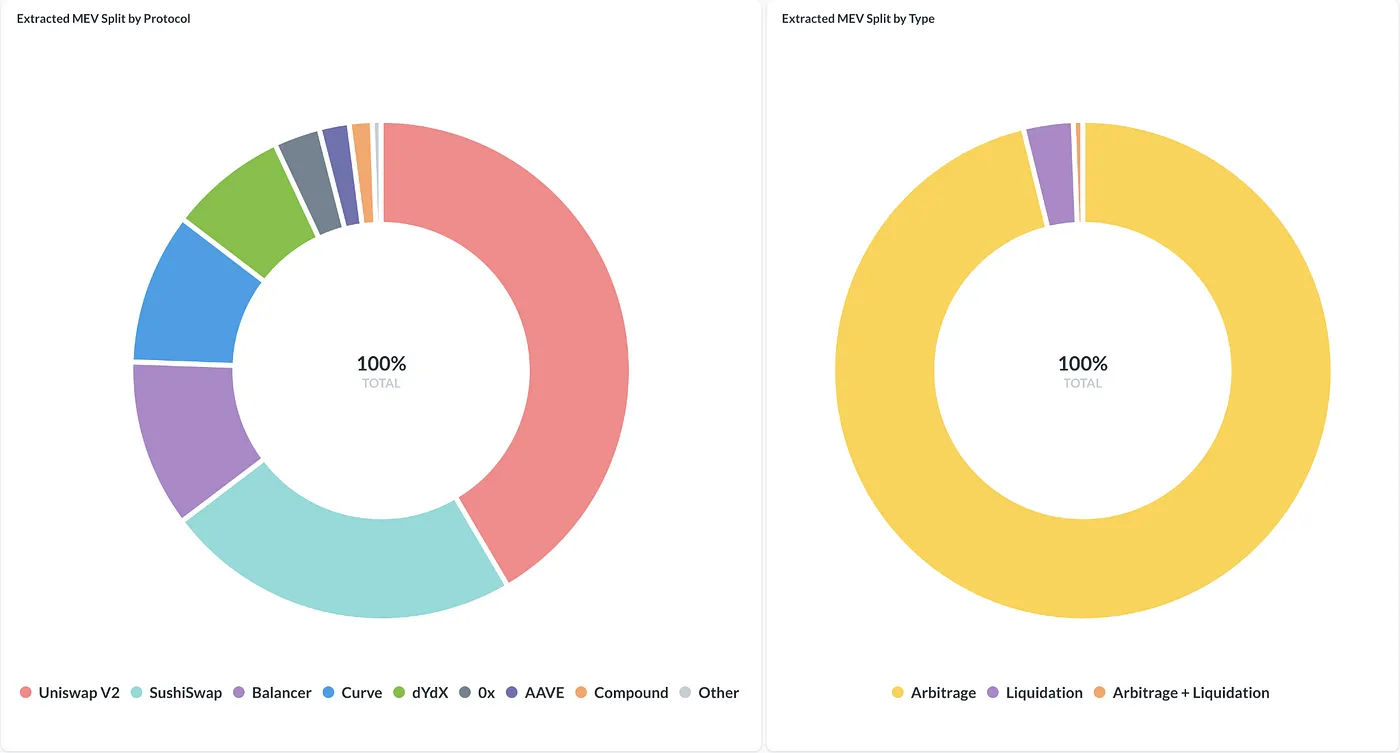
If we look at the origins of the humongous aggregate MEV value, we would discover that almost all of the MEV activities (97%) come from arbitrages, namely, arbitragers exploiting the price differences among different DEX protocols. It certainly makes sense as positions move in and out of the liquidity pool with such a high volume daily in the DeFi world, causing price distortion within the LP pools, and therefore give way to the arbitragers for the pure profit opportunity.
From the protocol distribution, we can find out that the major DEXes, leading with Uniswap V2, SushiSwap, and Balancer, accounted for over 77% of the MEV transactions, confirming the previous dominating percentages in arbitrage MEV activities.
On the other hand, lending and borrowing protocols such as AAVE and Compound only represent 2.9% of the total MEV market space, mainly from the liquidation events incurred in the platform, which accounts for roughly 3% of the total MEV activities.
These previous findings corroborate with the research conducted by Qin, Zhou, and Gervais, and they have demonstrated that no sandwich attacks have been observed from Curve, Swerve, or 1inch exchanges, potentially due to the outstanding slippage control of the trading pairs for Curve and Swerve, and private transaction function done by 1inch exchange. Furthermore, on liquidation MEV activities, only 12.71% tried to back-run the victim transactions, while the rest 87.29% attempted to front-run the competing liquidation transactions.
Under the current paradigm, what we are facing is clear. Arbitrage-typed MEV activities account for the vast majority of the overall MEV space, and the most common strategy is still front-running. However, it is worth noting here that the current MEV detection scheme is yet to be perfected. In fact, what we are seeing from MEV Explore is merely a first version that only captures a portion of the total MEV happening on Ethereum today. As a result, it is still hard to evaluate the accurate percentage of Ethereum’s bandwidth that is wasted due to MEV activities. Future efforts must be made in order to present a clearer picture. I am excited to see more projects like MEV explore or sandwiched.wtf that make an effort to bring clarity to the still convoluted MEV market.
Next, it is time for us to explore the current solution set in mitigating the MEV problem.
Solutions on the Consensus Layer: Guarding the Decentralization of the Network
There is yet to be a community-recognized way to categorize the current MEV solution set. For this report, I’ll use Hasu’s category which separates the numerous MEV mitigation or prevention solutions into roughly three buckets: consensus layer solutions, P2P layer solutions, and application layer solutions.
The current innovations on the consensus layer is arguably the most ambitious one among the three solution buckets. The core theme of the consensus layer solution revolves around one central topic — reducing the consensus instability due to the miners’ misaligned interest.
As I have explained previously, the entire miner’s issue in the MEV argument is similar to one big agency problem that not only do the miners make the sole distinction in regards to the transaction sequence, but they can also benefit a lot more from the order manipulation or block reorgs than just being the “benevolent dictator” and only collects the gas fee. On this note, it is possible to speculate that the EIP-1559 proposal is only another driving force pushing the miners into adopting more of the order manipulations.
There have been proposals that call for structural updates in the Ethereum core client, including a time-blocked mempool design which divides the current mempool into different blocks ordered by time, allowing the transaction on block T to be executed only after the entire block T-1 has been cleared. Nevertheless, judging from the past history of the Ethereum updates, implementation like this will take a long time before making its way to production. Hence, we will be focusing on community driven solutions including Flashbots (MEV-Geth), MEV-SGX, Fair Sequencing Service, Reorgs-as-a-Service, and finally dappled upon privacy solutions including timelock encryption, threshold encryption, and etc.
Flashbots (MEV-Geth)
One of the most discussed MEV solutions is perhaps Flashbots. As a R&D organization, Flashbots has a grand road map planning ahead, however, their current solution, MEV-Geth, builds upon the idea to democratize the MEV space. Why do I say this? Because, before Flashbots, searchers have been fighting in priority gas auctions (PGA), continuously bidding up fees to have their transaction recorded on block. And this was easily decided by whoever had a better view of the mempool, which would simmer down to the good methods used for extracting data from the “dark forest”, and executing on it. MEV opportunities would only be controlled by a few parties who had a good view of the mempool. These orders are then sent to miners to validate and add on-chain. However, only 1 transaction, the winner of the auction, will be able to capture the arbitrage opportunity. The rest of the orders, having not won this gas bidding auction, will then be cancelled and fail to land-on chain. It would be all good if that was all there is to it, but cancellations and failures lead to negative externalities that result in higher gas fees and more block space being used.
Now comes MEV-geth, the solution created by Flashbots. On a high-level, MEV-geth is effectively an API that consolidates all these MEV opportunities, and gives searchers a battleground to fight for the arbitrage opportunity. MEV-geth takes this battle off-chain, they identify all these flashbot bundles that searchers send, then analyses them, and they try to simulate these bundles being added to a block. Bundles are added according to the gas price listed, and ultimately, the bundles would be sent to a miner to validate the transactions.
To dig in deeper, I will explain further on the concept of MEV-geth, and bring you along the process. I mentioned bundles earlier, bundles are a group of transactions that searchers send to a miner, that includes their own, someone else’s or some other transaction from the mempool, or other sources. Searchers can slot their transaction into any part of this bundle, perhaps before someone else’s. Bundles have 2 main properties. Firstly, they allow transaction order preferences, targeted ordering of their transaction within their bundle. And secondly, either all or none of the bundle will be included on-chain. What happens next after a searcher has decided on their bundle? They will send their bundles to MEV-geth. MEV-geth will then run it through their parallel worker system, imagine 1 worker creating a block with 1 bundle, then another worker creating a block with 2 bundles, all the way with nth bundles. All of these workers are instances of a software running. These workers will simulate the bundles off-chain, adding them on top of each other one by one, depending on the bundles and the gas prices offered. They will take the highest gas price bundle and place it in a block, then the second highest gas price bundle and place it below that, so on and so forth, until the block is completed. Once these are finalised through MEV-geth, Flashbots will send these bundles to the miners via a private relay, and no longer through the public mempool. Effectively keeping it away from the eyes of sandwich bots and other malicious parties. Once it reaches the miner, the miners will validate these bundles, and put them on-chain.
Unfortunately, not all searchers stand a fair chance in MEV-geth. Flashbot introduced their reputation system, where searchers are split into 2 queues, high priority and low priority. Flashbots has a record on-chain of every searcher that uses their service. Each searcher is then ranked according to the frequency of high quality bundles submitted to MEV-geth. Therefore, high priority queue is usually given to a searcher who submit high quality bundles on a regular basis. This leaves new searchers who are using the service for the first time to fend in the low priority queue, where DDOS mostly reside. I will explain more about DDOS and its implications on miners in my third point below.
Through this process, we can see that Flashbots’ MEV-geth addresses 3 things. Firstly, it took this battle off-chain, and only the bot that is going to capture this MEV opportunity lands on-chain. Resulting in no cancellation or failures on-chain, which makes MEV efficient and reduces the average gas price. Secondly, it fosters the growth of the MEV scene, Flashbots has turned the competition from having the best view of the mempool to instead operating on gas-efficiency. Thirdly, a factor that is usually overlooked, and pertains to the benefit of the miners — protecting the miners. Oftentimes searchers are paying for their bundle through smart contract transfer instead of gas price, and because of this, the miner has to expand computational resources in order to find out if a bundle is good or not. However, this is based on a relationship of trust that the searcher is sending a high quality bundle to the miner. Miners are wary of this because there could be instances where miners get DDOS by malicious searchers, who basically spam them with low quality bundles that do not pay the miners anything, and force miners to expand computational resources to find out if the bundles are good. Flashbots are taking on this risk for the miners in their MEV-geth, because they are doing the job of simulating every bundle before sending it to the miners. Essentially, they are providing miners with protection against these malicious searchers. Moreover, malicious searchers that send DDOS are constricted to the low priority queue, making it even harder for them to reach miners. This protects the good faith between Flashbots and the miners, providing the essential trust that is required to send transactions through private relay to these miners.
Over time, we see that the average gas fees it takes to capture an arbitrage opportunity has come down, and this is one of the main goals of MEV solutions.
MEV-SGX
MEV-SGX is another product from Flashbots, but it is currently still in the works at the very early stages. MEV-SGX is actually a collaboration between Flashbots and Intel’s Software Guard Extension (SGX). Natively, SGX functions as a hardware-based memory encryption tool that separates specific application code and data in memory. It lets users allocate a private region of memories, called enclaves, that protects data from processes running at higher privilege levels.
MEV-SGX aims to provide a secure, private and permissionless MEV extraction process involving miners and searchers. Before searchers seek MEV arbitrage opportunities, they will first check via cryptographic attestations that both them and the miners are running the right software in an SGX, then exchange public keys. From here, searchers will find MEV, and craft a bundle of transactions for the miner to extract, along with the transaction fee for the miner. Searchers then generate a block and a block witness using their node, and place their bundle at the top of the block. Subsequently, they will input both the block and the block witness into SGX. On the searcher’s SGX side, SGX will use the block witness to verify that the block is valid and profitable for the miner. Once determined, 2 things will happen.
Firstly, searcher’s SGX will generate an unencrypted truncated header hash and coinbase difference. This will be passed on to the miner’s SGX where it will determine the most profitable block using coinbase difference. Then the miner will pass on the truncated header hash of the most profitable block to the miner’s workers to perform Proof of Work. Proof of Work solution will be provided once done. Secondly, searcher’s SGX will encrypt the searcher’s block with the miner’s SGX’s public key. The encrypted block will be passed on to the miner’s SGX. Here, the Proof of Work solution provided earlier will be used to decrypt encrypted block. Miner’s SGX will then seal the Proof of Work in the block and export it outside the SGX system. Lastly, the process ends when the decrypted and sealed block is propagated to the blockchain.
Chainlink Fair Sequencing Service
Fair sequencing service uses a simple idea. If it is too centralized to let one node decide the sequence of the orders within a block space, just divide the tasks among a few parties and decentralize the task. One of the popular implementations of the fair sequencing is done by ChainLink.
Chainlink’s fair sequencing service has just one goal, and that is to ensure fair fees to users when they trade. Before the fair sequencing service, transactions enter the mempool in a Layer 1 system, the miner picks up the transaction based on the gas price or some other metrics determined by a miner, and decides how it will be sequenced. However this poses a problem of centralization. Chainlink’s fair sequencing service helps to decentralize the process of sequencing transactions by leaving it up to a decentralized committee to decide on the order of the sequence. The committee is formed from Chainlink’s existing oracle network committee members, they already have the trust gained from users, and that makes them a good choice. How does it work? In the first phase of fair sequencing service, called Secure Causal Ordering, users will send their transactions directly to the committee members in an encrypted form. Encrypted on a public key belonging to a committee, and a corresponding private key that is shared in a threshold way among the committee members. The committee then decides in aggregate how to sequence these transactions off-chain, validates them on-chain and then decrypts them. The whole idea is that no node will see the gas price or transaction price before the transaction is sequenced, and this prevents a vast variety of MEV arbitrage opportunities from happening, because they don’t know the gas price. However, this method does leak some crucial information such as the metadata of the transaction, which could lead you to identify the account of the user. In addition, this method also does not stop searchers from doing blind front-running.
How exactly does the committee decide the order of the sequence? In phase 1, it’s not entirely concrete, and it relies on the sole discretion of the committee members. Hence, noticing this, Chainlink is currently in the works of the phase 2 of the fair sequencing service called Aequitas ordering. It supposedly uses the consensus protocol in a black-box way, and transactions are sequenced according to the super-majority time of they are received by the committee. This method prevents metadata from being leaked and covers the limitations of phase 1. The limitation of phase 2 is that it is sensitive to network adversaries, like a company that controls the internet that the committee member is using. However, the proposed usage of phase 2 Aequitas ordering, is actually in conjunction with phase 1 Secure Causal Ordering. They are made to complement each other and provide a more robust system of sequencing.
Chainlink’s Fair Sequencing Service is actually very similar to Cowswap’s model. Both of them employ off-chain tactics to decide the sequencing, and rely on a group of workers that help sequence them together to provide the best executable price to the user. In essence, MEV is passed on to these workers to help minimize MEV and provide a good execution price.
Onwards: Reorgs-as-a-Service
To understand Reorgs-as-a-service we have to first know what block re-organisation means. Block reorgs typically happen when 2 miners are validating the same block at about the time. What happens then is Ethereum will choose the longer chain, connect it to the parent block that is already connected to the main chain, and forgo the other shorter chain. The shorter chain is what is known as an orphan block. Conflicts like these happen commonly due to the slow broadcasting of confirmations across the network, and it is inherently built into the Ethereum blockchain to rectify the issue of miners mining the same block. To put it simply, when this is done deliberately, it is called a time-bandit attack. Where miner B wishes to take MEV from another miner A. Miner B does this by mining a separate, and longer chain, and connecting it to the parent block of the miner A. This effectively kicks out miner A’s chain, and leaves his chain as an orphan block. One instance of this almost happening on a large scale, would be Binance’s attempt to organise a large-scale reorg to recover 7000 BTC lost in a hack in 2019. For such a reorg to take place, firstly, the chain used to reorg the previous chain would require more than 51% of the total hashpower available on the network. Why more than 51%? Because while the rest of the 49% of miners are mining a block, 51% of the other miners would be mining a few blocks faster than the rest. Essentially creating a longer chain than 49% of the miners, and by default, the whole network would accept the longer chain. Thereby, allowing the reorg chain to connect to the main chain, and reversing all the transactions that happened on the original chain. And secondly, the user would have to give enough incentives for the miners to take up this reorg. However, in the end Binance did not go through with it, but it highlights some key issues regarding its feasibility that we will discuss down below.
Firstly, you need a ton of hashrate in order to force the network to accept another chain. Although the minimum is 51% of the network’s hash rate, you would need closer to 100% for this to have a higher chance of succeeding.
Secondly, you would have to give miners enough incentives or “bribe” to do this, but the resulting amount that you get back might not be enough to cover the high gas price paid to miners.
Thirdly, the longer it takes to propose and execute a reorg, the lesser the possibility of reorg happening. Every time another block gets validated from the target block, the incentives to reverse those blocks would have to increase, and the hashrate that you would need would also increase. In the case of Binance, Femboy Capital speculated that they were 50 blocks away from the target block, and therefore the incentives they would have to give to the miners to execute this reorg would have outweighed the 7000 BTC that was lost. Plus, they would need the cooperation of the majority of miners within the bitcoin network to capture such a high hashrate.
Fourthly, it would hurt blockchain’s decentralised and immutable nature and cause people to not believe in it’s fairness. Deliberate large scale reorgs would prove that the network is not truly decentralised and it could be attacked by a single entity at any moment. Such a thought would easily give a negative perception that the network could be manipulated and destabilise the consensus. In other words, this would lead to a drop in value of ETH and BTC.
Fifthly, time-bandit attacks or reorgs would not usually be instigated by miners because it’s a zero-sum game between miners. One miner would conduct the reorg at the expense of another miner, and they are effectively hurting themselves. In addition, many of these miners also stake ETH or BTC and provide security for various blockchains. In the long-term, it would not be an economical choice because their own cryptocurrency value would fall, and their reputation would be at stake.
Lastly, we talk about doing this time-bandit attack on ETH2.0, where it moves away from Proof-Of-Work(PoW) to Proof-Of-Stake(PoS). PoS does not use the same “longest chain” metric like PoW, but instead, it is driven by votes from the validators. Hence it gives validators the autonomy to let this reorg pass, or stop it. For the reorg to pass through, you have to coordinate most of the validators in the network, which would be more difficult than PoW where you can just dominate the network alone by having a very high hashrate.
All in all, Reorgs-as-a-service is a very controversial topic, and most of the community seem to be against it rather than for it. Just like how Flashbots created MEV-geth to make MEV more efficient, Reorgs-as-a-service has the same goal. I am also against such an application, because of the reasons stated above. However, if it’s application does not disrupt the fundamental goals of blockchain, I believe it could become a great impetus for MEV efficiency.
Solutions on the P2P & Application Layer
As an investor, I have more faith in the application layer solution not only because they are closer to the users — providing direct benefits to ease the trouble from MEV, but also because MEV can be more pervasive in the application layer. Many people debated that there is no MEV on BSC or other chains utilizing different consensus mechanisms than Ethereum’s PoW (PGA). It is true that the miners in these specific ecosystems may choose not to participate in the MEV hunt, for whatever reasons out there. However, the application layer MEV competition, involving the bottom two stacks from Figure 2, will always be present. Therefore, it can be argued that the application layer solutions have more potential or a better angle in solving the MEV issue.
The current solution set in the application layer is nothing new. It revolves around the central idea that we have visited previously. Instead of Flashbots organizing and selecting a group of miners and searchers to extract and directly distribute MEV profits among the two parties, the protocols can also establish a subset of miners who can take the orders directly. In this case, the protocols act as a searcher and the MEV profits can then get distributed to the miners and users who are in the network.
Private Relays: The Taichi Network
Taichi Network is a private relay between Ethereum and the Spark Pool, the current second largest Ethereum mining pool in the network. There are also similar services provided by protocols/infrastructure providers such as bloXroute, with the protocols assembling their own group of trusted miners.
The idea of these private miner networks is very simple. Users instead of sending their transactions to Ethereum’s public mempool (by using the public RPC in the Metamask, for example), directly send a private transaction to the Taichi Network by changing their wallet’s RPC or using Taichi’s API. This transaction then goes to a private mempool / relay where a portion of the Spark Pool’s hash rate would be allocated to fill transactions from this relay. The transactions going through the Taichi Network would not be broadcasted to the public mempool, thereby shielding the potential MEV threat from predatory bots and miners. It is worth noting here that although the Taichi Network markets itself as the private relay, the transactions in Taichi’s mempool are still very much visible to all of the Taichi participating nodes. As a user, you just have to trust these nodes that they are not going to exploit the MEV opportunity under Spark Pool’s command.
The entire idea of Taichi or other similar private relay services surely sounds fantastic, as it essentially eliminates all MEV threats within its sub-network. However, there are of course problems with this design. The most worrying problem of this private relay service is that it fosters the centralization of the mining pools with the increased usage and thereby endangering the entire blockchain’s integrity through time. Moreover, the network is not 100% bulletproof. It is possible that the block bundled by the Taichi’s miner becomes an uncle block and then becomes visible to the entire public mempool waiting to be repackaged. This design also cannot prevent block reorgs, but this perhaps is of a lesser concern to the user at the time we stand in today.
For Taichi Network, the best use case I can see is outlined in Sam’s article — a group of white hats trying to save the funds from endangered protocols. It is almost completely safe from MEV, and one transaction has almost nil effect in terms of the network’s overall decentralization level. For the average users, the transactions going through Taichi may be slower than using the public RPC as although you are paying the same gas (yes, PGA is still how Taichi arranges order), but you are exposed to far less hash rates compared with the entire Ethereum Network. In the meantime, you have to give all your trust to the Taichi Network and Spark Pool, and more importantly, you have to be aware that the transactions you sent are pushing the network towards a more centralized state — if you really care about decentralization and DeFi, this is perhaps something you should be aware of using such services.
The Searcher’s Union: Keeper DAO
If Keeper DAO names their protocol to Searcher DAO, then it would immediately make more sense. Many people misunderstood Keeper DAO as the application layer’s Flashbots, and it is simply not the case.
On the grand scale, Keeper DAO’s goal is to coordinate searchers in combating against the PGA mechanism, although this is yet to be realized.
Currently, the protocol’s main component is a flash loan pool providing necessary funds for the searchers to conduct arbitrage. Searchers execute arbitrage opportunities and return the profits (full or partial) for $ROOk (Keeper DAO’s native token) rewards determined by the percentage of the total profit earned. Currently, as of July 2021, there are in total of 5 pools providing an aggregate of 240m funds.
Recently, Keeper DAO has also implemented its Hiding Game mechanism which allows the users to get MEV protection for their trades and collateral positions. For transaction protection, users can submit a limit order to a Keeper DAO relay, and the Keepers in the network (requires whitelisting as of now) will execute the trade through 0x’s RFQ (Request for Quote, a stripped-down version of limit order that can be matched by 0x’s order book engine) API and try to extract the MEV for this specific trade. Upon success, the user will get not only its exchanged token at the requested price, but he or she will also earn $ROOK rewards for a portion of MEV profit extracted by the searchers. On the other end, the searchers will also get $ROOK reward, but the entirety of the profit will go back to the Keeper DAO vaults. As the reader may see, this is very similar to the BackRunMe.com service provided by bloXroute, allowing users to actively seek MEV exploits from searchers and miners and split the revenue between the parties. In BackRunMe’s case, multiple searchers can submit potential MEV exploit proposals, and bloXroute will rank the highest MEV transaction bundle before forwarding this finalized MEV bundle to its own private relay for execution.
For collateral protection, Keeper DAO’s solution is to set up a JITU (Just-In-Time Underwriter), a bot that monitors users’ collateral position in real-time for any liquidation risks. Upon users’ collateral is nearly reaching the liquidation level, Keeper DAO will provide an emergency fund from its vaults for short-term liquidity needs. If the user can not reimburse the liquidity provided, then at the second stage, a white-listed searcher would join the PGA war and try to execute the liquidation for the user. Similar to the previous models, the revenue also gets split by the participants.
The entire Keeper DAO’s model relies on several key premises. First, it assumes PGA is the only game that the searchers participate in. Second, miners will not actively participate in the MEV extraction game. Thirdly, with the vaults, the searchers can have endless resources driving out the non-ecosystem searchers out of the PGA war, forcing them to join the network. Finally, with collaboration (the Collaboration Game, the grand trophy on the Keeper DAO’s road map), searchers take turns to execute MEV arbitrages and therefore maintain the gas fee at a lower level.
As an investor, I am very conflicted by the Keeper DAO’s model. On one side of the coin, this model is very well designed for any blockchains with miners acknowledging the non-involvement of the active MEV extraction (BSC, HECO, or POS chains with higher degrees of centralization). By actively connecting users and searchers, the users can gain the most benefit as their transaction can not only be executed with a lower gas price, but they can also share a part of the MEV revenue extracted by the white-listed searchers.
However, on the other side of the coin, there are many flaws that I see that exist in the system:
- Miners are being ignored in the puzzle: For the majority of the blockchains, miners have the incentive to actively participate in the MEV extraction game. Flashbots can only alleviate a portion of the problem, but the vast majority of the miners can still take action and search for MEV opportunities themselves. Assuming miners are all benign and ignoring miners’ effect in the MEV extraction assembly line is an oversimplification of the problem. I believe it is important for Keeper DAO to establish a relationship with the Flashbots team and loops the miners into the game.
- Searchers now utilize more sophisticated methods in extracting MEV: PGA is not the only mechanism that exists that searchers play to extract MEV anymore. As the PGA game has been almost impossible for the majority of the searchers to win, recently, more and more searchers utilize private relays (Flashbots, for example) to facilitate their MEV bundles in order to achieve faster and safer transactions. Because of this, according to MEV Senpai, only sandwich bots can still survive in the public mempool, whereas the majority of the front-running and back-running searchers have already moved to the private relay. For Keeper DAO, this not only means that it will be extremely hard for participating searchers to find the profitable transaction to exploit and resulting in searchers waiting for hiding game order feeds, but it also means that at the current stage without searcher collaboration, it is possible that the Keeper DAO searchers are just competing against each other without any positive externality.
- The Keeper DAO’s pool is not the determining factor in successful MEV extraction: as the central component of the Keeper DAO structure, the vaults are sometimes not so important for the searchers. One reason behind this is that in order for searchers to utilize vault funds, it needs more transactions to be included in the overall MEV bundle, thereby forcing the searchers to pay a higher gas fee comparing with other searchers who use their own funds.
- Keeper DAO plays the all-or-nothing game: overall, if we look at the current incentive scheme for Keeper DAO, we would realize that Keeper DAO puts itself in a rather awkward position. If a searcher is good enough, he or she can directly execute the opportunity via private relay without sharing the profit with the users. Most of the good MEV bots have their own funding sources, even though they really need funds, there are many flash loans available to use. Then logically, the rest of the mediocre bots would join Keeper DAO’s network and participate in the PGA war. However, realistically, it is possible that they simply can’t generate much profit from the mempool as there are still many non-Keeper DAO bots out there. This lowers Keeper DAO’s overall vaults’ yield, disincentivizes further participation from all participants within the ecosystem. Finally, if the searchers are all looking for opportunities within the Hiding Game’s relay, this lowers the overall expectancy of the searchers getting the profit opportunity, driving the keepers away.
Part Deux?
After writing the part I of this MEV analysis (finished August 2021), I find myself exhausted in the search for a perfect solution for MEV. As I cannot find a perfect answer, this draft stays in my computer for almost half a year, and I was not intended to let the public see the imperfect puzzle.
Now, realizing that there may not be a perfect MEV solution at the end (and thanks Baojie for your nudge), this article gets to see the light. Nonetheless, this is not the end. The article itself will be updated once I find any updates on the current content and projects, and maybe we will have a part II of MEV discussion, but who knows.
Anyhow, if you’ve read this far, you must be really interested in the matter of MEV. You should perhaps check out any content posted by Flashbots. They are by far the authority on the MEV issue. Thanks for you patience, and I hope I’ll see you again.